Security
| Created time | |
|---|---|
| Tags | A2C20Notes |
Encryption fundamentals
- Encryption can be used as a routine procedure when storing data within a
computing system. However, the focus in this chapter is on the use of encryption when transmitting data over a network.
- There are three issues that will be considered in this chapter:
- is the encryption algorithm sufficiently robust to prevent the encrypted data being decrypted by some unauthorized third-party?
- how is it possible to ensure that a secret key remains secret?
- how can the receiver of a communication be sure who sent the communication?
Plaintext:
data before encryption
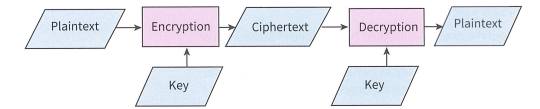
Ciphertext:
the result of applying an encryption algorithm to plaintext, also known as encrypted or encoded information
Key:
a piece of information, usually a string of numbers or letters that are stored in a file, which, when processed through a cryptographic algorithm, can encode or decode cryptographic data.
Encryption:
- the process of encoding data or message so that it can not be understood by others
Security concerns
- There are a number of security concerns relating to a transmission.
Confidentiality: Only the intended recipient should be able to decrypt the ciphertext.- Authenticity: The receiver must be certain who sent the ciphertext.
- Integrity: The ciphertext must not be modified during transmission.
- Non-repudiation: Neither sender nor receiver should be able to deny involvement in the transmission.
- Availability: Nothing should happen to prevent the receiver from receiving the transmission.
- This chapter will consider only confidentiality, authenticity and integrity.
- The confidentiality concern arises because a message could be intercepted during transmission and the contents read by an unauthorized person.
- The concern about integrity reflects the fact that the transmission might be interfered with deliberately but also that there might be accidental corruption of the data during transmission.