Hardware and virtual machine
| Created time | |
|---|---|
| Tags | A2C18Notes |
Logic gates and circult design
Logic gates:
A component of a logical circuit that can perform a Boolean operation (logical function).
- AND GATE: A.B = X
- OR GATE: A + B = X
Half-Adder
A logic circult whose output is dependent only on the input values.
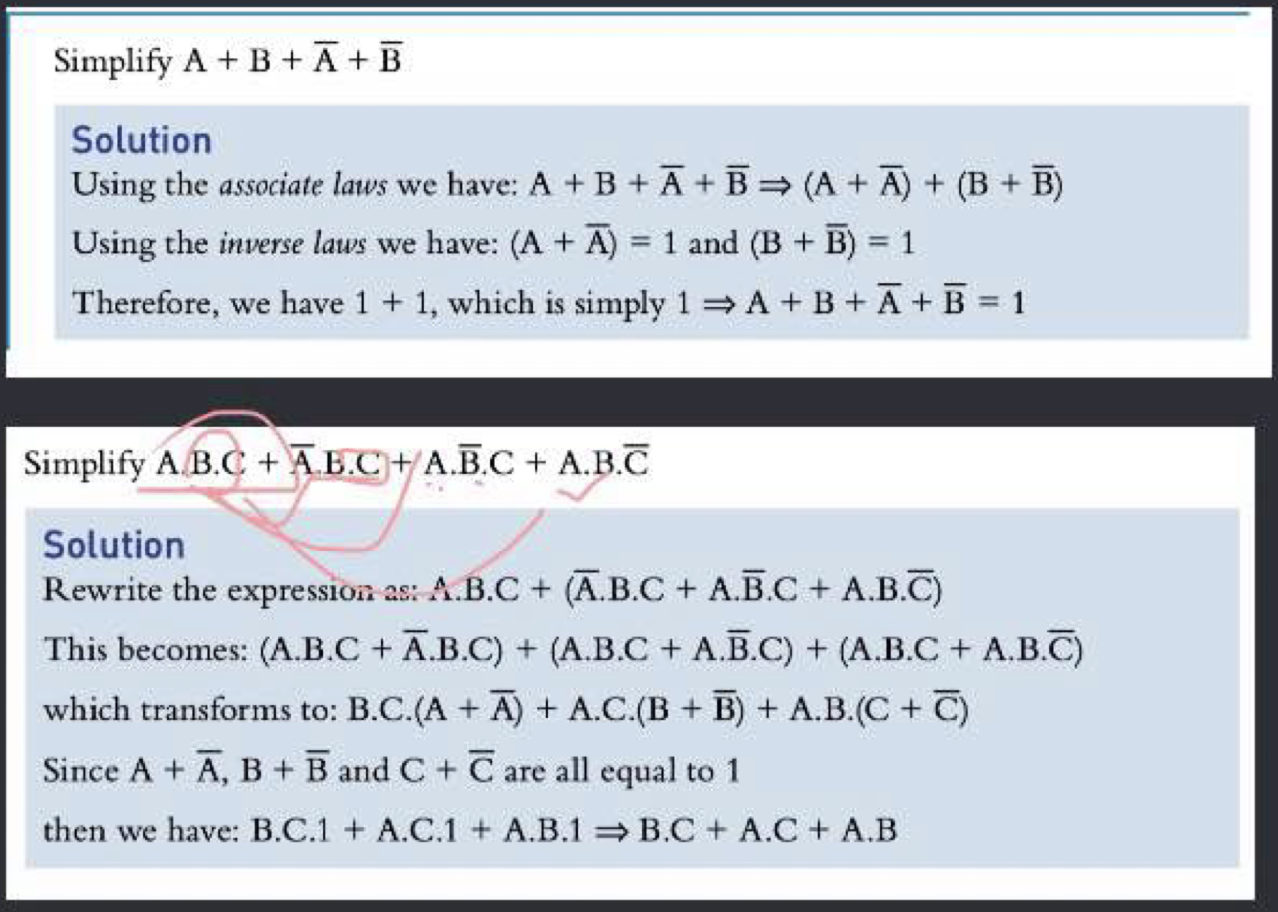
Boolean algebra
- Double Complement:
- Identity Law
- Null Law
- Idempotent Law
- Inverse Law
- Commutative Law
- Associative
- Distributive Law
- Adsorption
- De Morgan’s Law
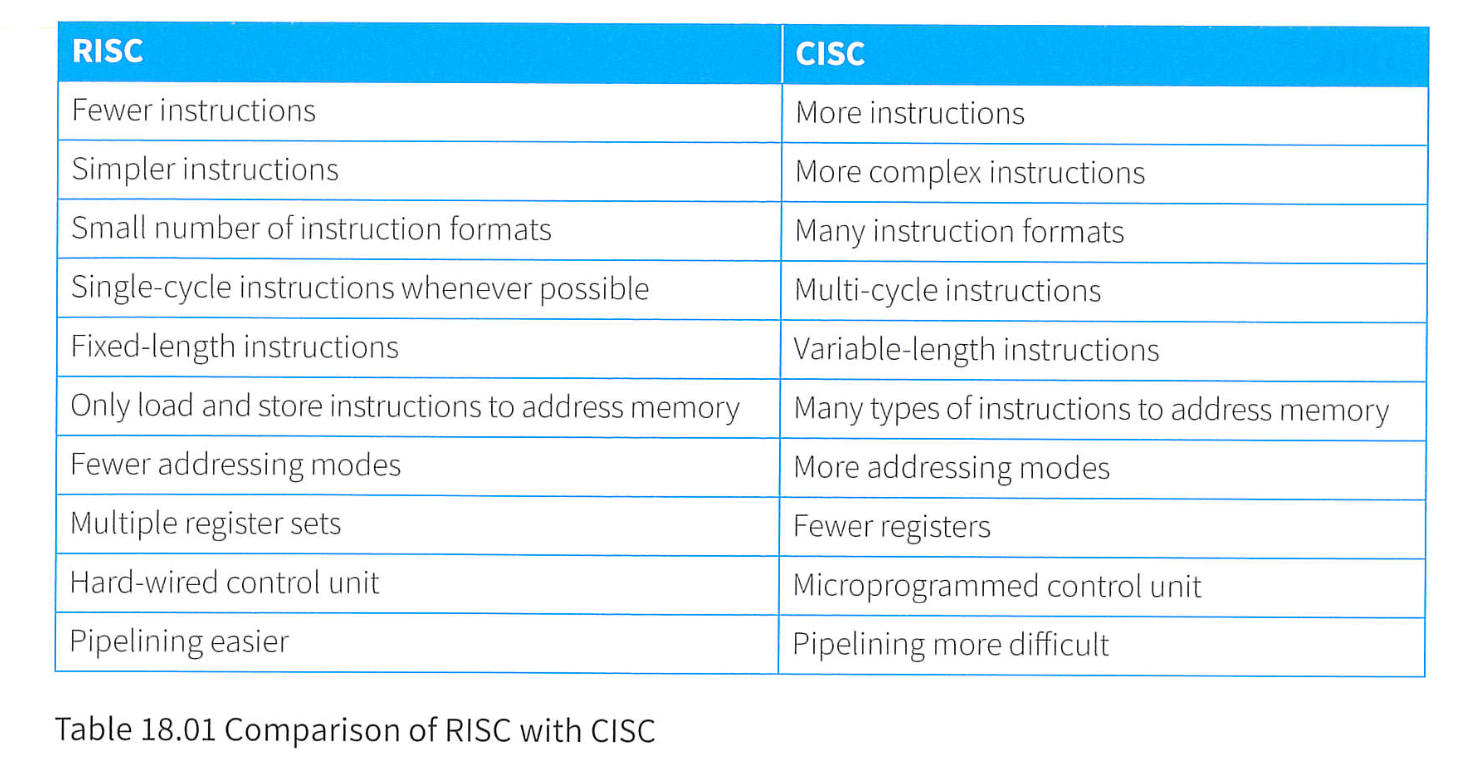
CISC and RISC
- CISC: Complex instruction Set Computer
- RISC: Reduced Instruction Set Computer
What is Instruction Set?
- Set of all instructions written in machine code that can be recognized and executed by a given processing unit/CPU
Points to note
- For RISC the term 'reduced' affects more than just the number of instructions.
- A reduction in the number of instructions is not the major driving force for the use of RISC.
- The reduction in the complexity of the instructions is a key feature of RISC.
- The typical CISC architecture contains many specialized instructions.
- The specialized instructions are designed to match the requirement of a high-level programming language.
- The specialized instructions require multiple memory accesses which are very slow compared with register accesses.
- The simplicity of the instructions for a RISC processor allows data to be stored in registers and manipulated in them with no resource to memory access other than that necessary for initial loading and possible final storing.
- The simplicity of RISC instructions makes it easier to use hard-wiring inside the control unit.
- The complexity of many of the CISC instructions makes hard-wiring much more difficult so microprogramming is the norm.
See more at https://learnlearn.uk/alevelcs/risc-vs-cisc-processors/
Pipelining
- One of the major driving forces for creating RISC processors was the opportunity they would provide for efficient pipelining.
- Pipelining: instruction-level parallelism
- What does it mean by parallelism?
- The underlying principle of pipelining is that the fetch-decode- execute cycle described in Chapter 5(Section 5.06) can be separated into a number of stages. One possibility is a five-stage model consisting of
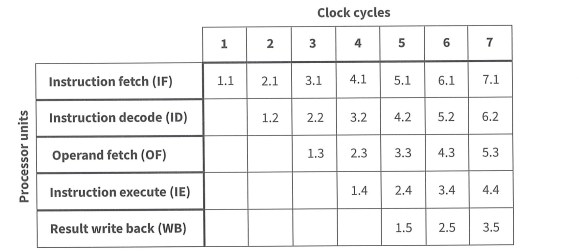
Pipelined processor and interrupt handling
- One issue with a pipelined processor is interrupt handling.
- The discussion in Chapter 5 (Section 5.08) referred to a processor with instructions handled sequentially. This approach where a check for any interrupt is made following the execution of an instruction is applicable to a CISC processor. It would also be applicable to a RISC processor if there were no pipelining.
- However, this is an unlikely circumstance. In the pipelined system described above there will be five instructions in the pipeline when an interrupt occurs.
- One option for handling the interrupt is to erase the pipeline contents for the latest four instruction to have entered. Then the normal interrupt-handling routine can be applied to the remaining instruction.
- The other option is to construct the individual units in the processor with individual program counter registers. This option allows current data to be stored for all of the instructions in the pipeline while the interrupt is handled.
The basic computer architectures
- A well-established approach to describing different computer architectures is to consider the number of instruction streams and the number of data streams. This leads to four different types :
• SISD
• SIMD
• MISD
• MIMD
SISD
Single Instruction Stream Single Data Stream
• The functioning is purely sequential with no parallelism
• Only one single process unit
• A single instruction is executed on a single data stream
- The original Von Neumann Architecture was SISD.
• Advantages:
• Cheap
• Low power consumption
• Disadvantages:
• Limited speed due to being a single core
• User:
• Microcontrollers
• Older mainframes
SIMD
Single Instruction Multiple Data (SIMD)
• A single instruction is executed on multiple different pieces of data
• These instructions can be performed sequentially, taking advantage of pipelining, or in parallel using multiple processors.
• Modern GPUs, containing Vector processors and array processors, are commonly SIMD systems.
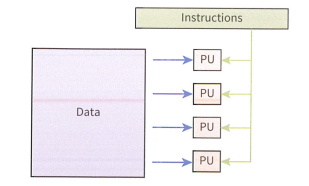
SIMD
Single Instruction Multiple Data
Advantages:
Very efficient where you need to perform the same instruction on large amount of data
Disadvantages:
Limited to specific applications
Uses:
GPUs
Scientific processing
MISD
Multiple instruction single data
• Multiple processors work on the same data set performing different instructions at the same time
• Advantages:
• Useful where real time fault detection is critical
• Disadvantages
• Very limited application so not available commercially
Uses
• Space shuttle flight control systems
MIMD
Multiple instruction multiple data
• Multiple processors perform operations on different pieces of data
• This means that serval different instructions can be executed at the same time, using different data streams
• Advantages:
• Great for situations where multitasking is required
• Disadvantages:
• Much more complicated architecture so more expensive
• Uses
Most modern PCs, laptops, smart phones
Massively parallel computer systems
• Used by large organizations for computations involving highly complex mathematical processing.
• Supercomputer
• Multiple processors
• Cluster
• Multiple computers
• Key features: extremely large number of individual processors working in parallel.
Flip-Flop circults
- All of the logic circuits you have encountered up to now are combination circuits (the outout depends entirely on the input values).
- We will now consider a second type of logic circuit, known as a sequentia circult (the output depends on the input value produced from a previous output value).
- Examples of sequential circuits include flip.flop circuits, This chapter wil consicer two types of fip-flops: sk flip flops and Jk flip-flops.
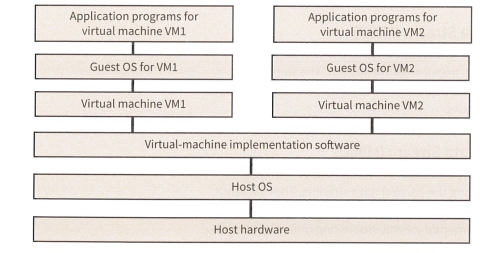
Virtual machines
- In computing, a Virtual Machine is the virtulization or emulation of a computer system.
- virtual machines are based on computer architecures and provide the functionality of a physical computer.
- a virtual machines is software, not hardware
- The process of creating and running a virtual machine is known as virtualization
- The computer that runs the virtual machine is known as the host. The virtualized system a guest
- Virtualization software, known as an emulator, creates a virtual implementation of the guest system on the host computer, providing the host with the functions and programs of the guest
- The emulator translates the instructions of the guest computer so that the host computer can understand them. (from hips://learnlearn.uk/alevelcs/virtual-machines/)
System virtual machine
System virtual machines
- System virtual machines emulate the software of another computer system completely
- They allow the host computer to have all the software functionality of the guest system.
- System virtual machines run the operating system of the guest system within the operating system of the host, allowing programs supported by the guest operating system to be run on the host computer.
- Example:
Users running Apple operating systems often use a Microsoft Windows virtual machine to run the Windows operating system on Apple computers to allow the windows app to run on an Apple computer.
Process virtual machine
- Process virtual machines emulate a single program.
- They are often used to support a programming language, allowing programs created in that language to run on a variety of systems.
- They are frequently used to emulate old video game systems and arcade games
Java virtual machine
- Many programs are written in high-level languages such as Visual Basic, C++,Python and Java.
- Before these programs can be run they need compiling. A compiler takes the high-level language source code and converts it into machine code.
- This machine code is a set of instructions specific to the processor architecture that the compiler is running on.
- As a result, this code can only be run on processors that share the same instruction set.
Benifits of VM
from mark scheme
- multiple guests OS can be used on the same computer
- Different instruction set architectures can be emulated on a single Computer
- a VM can crash without affecting the host machine
- There are security benefits // Trying a peice of suspicious software and if it is a virus, it will not infect the VM
- cost saving due to not needing to purchase extra hardware
- can run legacy applications that are currently incompatible.
drawbacks
from mark scheme
- a VM is less efficient / has pooper performance than real machines because of extra load on the host computer
- performance of the guest cannot be adequetely measured
- performance of the host is reduced.
- a VM may be affected by any weakness of the host machine costly and/or complex to maintain/implement/manage
- can not emulate some hardware